Starting yesterday, there have been numerous reports of people's Windows computers being infected with something called "All-Radio 4.27 Portable". After researching this, it has been determined that seeing this program is a symptom of a much bigger problem on your computer.
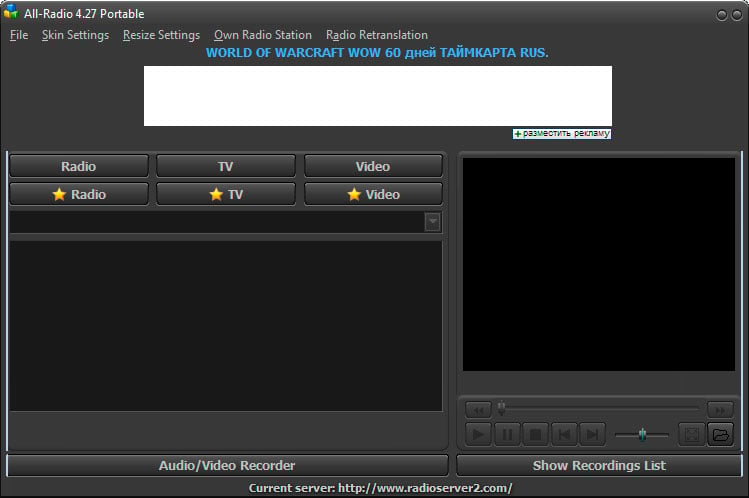
If your computer is suddenly displaying the above program, then your computer is infected with malware that installs rootkits, miners, information-stealing Trojans, and a program that is using your computer to send send out spam.
Unfortunately, while some security programs are able to remove parts of the infection, the rootkit component needs manual removal help at this time. Due to this and the amount of malware installed, if you are infected I suggest that you reinstall Windows from scratch if possible.
If that is not an option, you can create a malware removal help topic in our Virus Removal forum in order to receive one-on-one help in cleaning your computer.
Furthermore, some of the VirusTotal scans associated with this infection have indicated that an information stealing Trojan could have been installed as well. Therefore, it is strongly suggested that you change your passwords using a clean machine if you had logged into any accounts while infected.
For those interested in more information about the infection, you can read the rest of the article.
All-Radio 4.27 Portable infection installed through cracks
This malware campaign appears to have started yesterday when people began requesting help in the Malwarebytes forum. These help requests were from users who suddenly saw a program called All-Radio 4.27 Portable in Windows, but could not find a way to remove it.
While All-Radio 4.27 Portable appears to be a legitimate Russian online video and radio program, the malware authors have copied it and created an imposter to act as a front for other malware that is installed.
When malware removal expert, Aura, started helping these victims he noticed a common theme. Most of the users reported being infected after they downloaded and installed game cracks and Windows activation tools such as KMSpico.
When I checked all of the reported links, I found that supposed cracks were a "aimp" adware bundle. This adware bundle is what is most likely pushing the malware package.
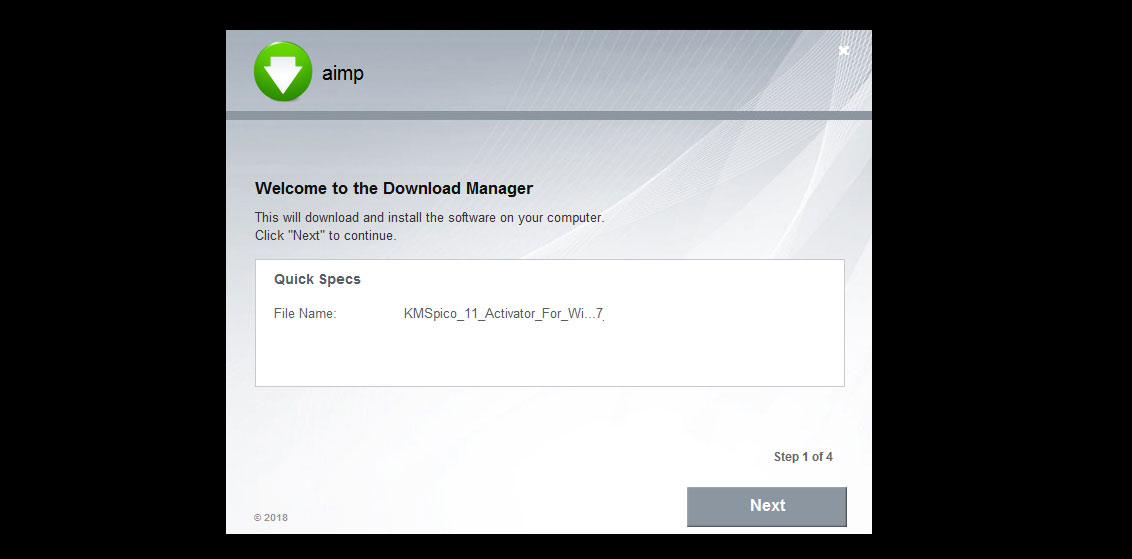
This malware package has a whole basket of goodies
From the research conducted by myself, Aura, and Elise, it was found that the infection will download and install a cascade of malware that ultimately infects a computer with a rootkit, a miner, a clipboard hijacker, a spammer, and other Trojan downloaders.
The main installer, which is virtual machine aware, will be installed in %AppData%\Microsoft\Windows\[random]\[random].exe and will inject a process into Explorer.exe. This process will then copy itself to %Temp%\allradio_4.27_portable.exe and display the All-Radio 4.27 Portable screen.

It will then download and install various files into the %Temp% folder and execute them. These downloaded files will ultimately install the following malware:
- A program that connects to https://iplogger.com/1kfvV6 for statistics purposes.
- A miner called file.exe that is injected into C:\Windows\Syswow64\svchost.exe.
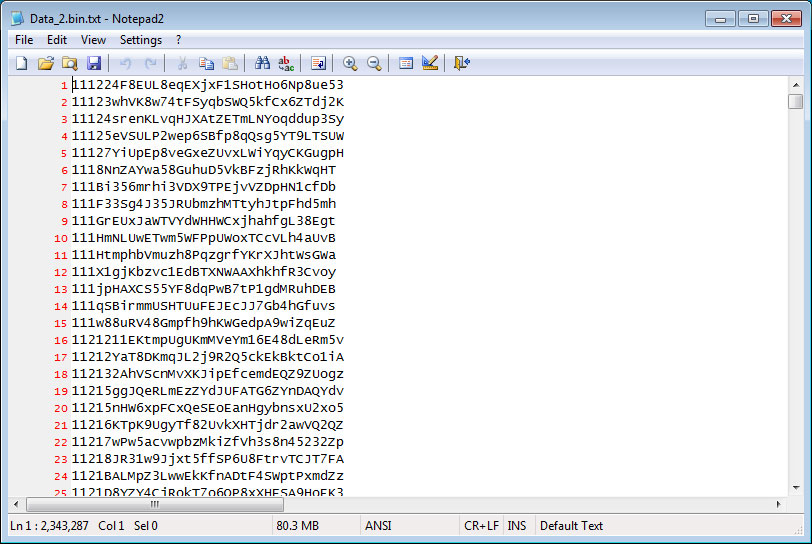
- Malware that monitors the clipboard for 2,343,286 cryptocurrency addresses, and if one is detected, replaces it with a different address under their control.
This allows the malware developers to steal the cryptocoins that are transferred to their account instead of the expected one. You can read more about this type of malware here. I also created a demonstration video below.

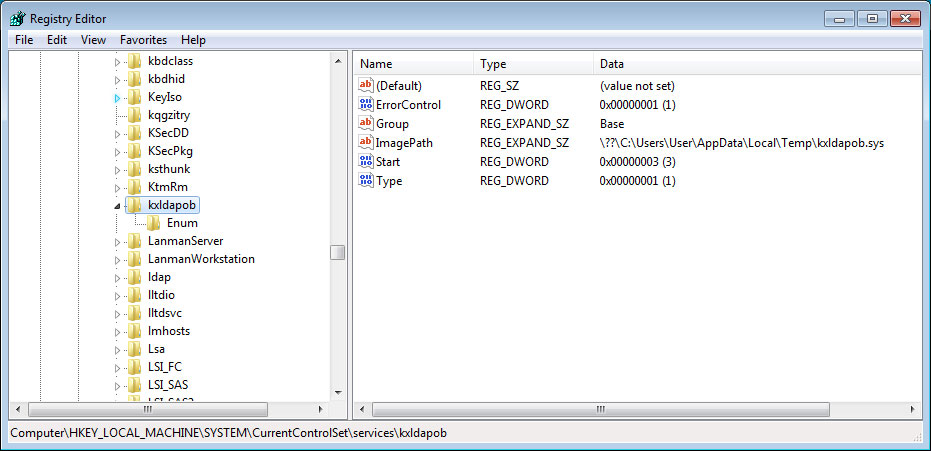
Portion of Monitored CryptoCurrency Addresses - A rootkit driver with a random file name under the %Temp% folder that hides itself and another service that has a display name of "wifi support". The protected service is created with the commands:
sc create fjuolnkd binPath= "C:\Windows\SysWOW64\fjuolnkd\wwvbmahk.exe /d\"C:\Users\admin\AppData\Local\Temp\A159.tmp.exe\"" type= own start= auto DisplayName= "wifi support" sc description fjuolnkd "wifi internet conection"
Rootkit Driver - A Trojan downloader that can download and install other malware.
- A Trojan that uses your computer to send spam.
According to some of the VirusTotal scans, some of the infections could also be information stealing Trojans. Therefore, if you have logged into any accounts while being infected, you may want to change your password at those accounts from a clean machine.
As you can see, this is a serious infection with malware that can potentially steal your account credentials, use your computer for mining, and download other malware on your computer. As it uses a rootkit to protect some of its functions, it indicates that the malware developer means business and we can expect to see this continue to be distributed. Therefore, be sure to clean your computer if you have any of the above symptoms.
Finally, cracks have always been a source of malware, especially for consumers. Due to this, it is strongly advised that you avoid cracks and other programs that can generate software licenses as they are commonly infected with malware.
IOCs
Hashes
Main Installer - Megasync.exe/allradio_4.27_portable.exe (random exec name): 9d891048dddda8a65de966c71f81464b20e402766aaee8a284da8d25c98270bd -
d3dx11_31.dll: 48b66dd02a336eb049a784b3fd1beb5312fb8c078b3729d49e92e3e986c98e91 - Clipboard CryptoCoin Hijacker
Logger.exe: 0cc32e6e6a407b2b69e1d89b3f005eecc54e238104725dcdcc8d3fc09c109bb4
Injected miner: cf8ef10678e63ffd02a5a35c84461d0195e0eed234bf9328eede52f3bef0e5f7
Hidden Service: 2e23ab52259e45eaced300811a6d6795db719b029d06b08ca7bac7d86cc289ad
Satamon.exe: 2c3eae980a88e7bb6a91f2b466856f612f34b8a37fac46bbbb52c0af0e695488
Adware bundles:
ffdc286711557df5f0bfd6a96744e93633d13fe45c02c240d5d6cf7531b21847
20bdef6e68bbec5ddeb7b893a9b4f387adbf2ee304963e905d98116a57334a41
Temp downloaders:
acf810c7bb3961fd42f5925fcd4417cb812eb6fdaad00c98830c522d54c7f6eb
084d4811c47a5dc36df59bfaf477e1f0bf3a9b3901877de1d1548c3343d1e4d6
ea92702d5fe168a57ccf5abbe6b9f5eca25f039e111db4b010183aa6909c38d2
2c3eae980a88e7bb6a91f2b466856f612f34b8a37fac46bbbb52c0af0e695488
Registry Entries:
HKCU\Software\All-Radio
HKCU\Software\All-Radio\Settings
HKCU\Software\All-Radio\Settings\TimeStamp 914BE45509E88CBE12C9C147B92F8928
HKCU\Software\All-Radio\Settings\CurrentLanguage English
HKCU\Software\All-Radio\Settings\skin name Cold
HKCU\Software\All-Radio\Settings\color 0
HKCU\Software\All-Radio\Settings\saturation 0
HKCU\Software\All-Radio\Settings\use skin 1
HKCU\Software\All-Radio\Settings\CurrentServer http://www.radioserver2.com/
HKCU\Software\All-Radio\Settings\ServersCount 8
HKCU\Software\All-Radio\Settings\resize 1
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\agwpyjho "C:\Users\User\gidulfmf.exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\DirectX 11 rundll32 %Temp%\d3dx11_31.dll,includes_func_runnded
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{E50B01A9-6717-4321-B6C1-3444E35D4419}
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{E50B01A9-6717-4321-B6C1-3444E35D4419}\Path \Opera scheduled Autoupdate 1427321617
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{E50B01A9-6717-4321-B6C1-3444E35D4419}\Hash BINARY SIZE=32 MD5=5520F781167B06815EF8BD54DD186F9C
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{E50B01A9-6717-4321-B6C1-3444E35D4419}\Triggers BINARY SIZE=352 MD5=83356B89B15EAB067435487A7B92FDBE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{E50B01A9-6717-4321-B6C1-3444E35D4419}\DynamicInfo BINARY SIZE=28 MD5=3068A03846DFF3649992C32FBA75E688
HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths\C:\Windows\SysWOW64\kqgzitry 0
Associated Files:
%Temp%\1A26.tmp.exe
%Temp%\A159.tmp.exe
%Temp%\allradio_4.27_portable.exe
%Temp%\F1BD.tmp.exe
%Temp%\lame_enc.dll
%Temp%\d3dx11_31.dll
%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\SATA Monitor.lnk
%AppData%\Microsoft\Windows\[random]\[random].exe
%AppData%\1337\file.exe
%AppData%\1337\Logger.exe
%AppData%\SATA Monitor\satamon.exe
C:\Windows\SysWOW64\[random]\[random].exe
C:\Windows\System32\Tasks\Opera scheduled Autoupdate 1427321617


Comments
phossler - 5 years ago
Read the removal instructions and noticed that PSI is still recommended step.
PSI is EOL and should probably be removed from all removal instructions
https://www.flexera.com/products/software-vulnerability-management/personal-software-inspector.html
"This product has reached End-of-life on April 20, 2018, and therefore, no longer available. Existing installations of PSI will no longer function and should be uninstalled."
Bleky - 5 years ago
Haven't seen such an aggressive malware for a long time.
Warthog-Fan - 5 years ago
So if you had done a full backup of your hard drive, including a System Image, would doing a total restore solve the problem? Seems like it would.
Lawrence Abrams - 5 years ago
That would pretty much solve any infection issue.
BitcoinWhosWho - 5 years ago
Are you going to make the 2,343,286 bitcoin addresses available anywhere?