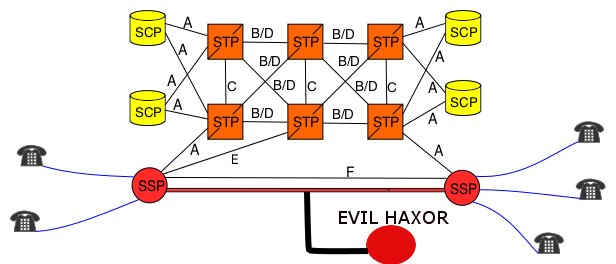
A documented weakness in Signaling System 7 has been shown to allow widespread interception of phone calls and text messages (SS7 is the public switched telephone network signaling protocol used to set up and route phone calls; it also allows for things like phone number portability). This weakness in SS7 can even undermine the security of encrypted messaging systems such as WhatsApp and Telegram.
In an April segment of 60 Minutes, Democratic Congressman Ted Lieu of California allowed hackers to demonstrate how they could listen in on his calls. In light of the mass leak of congressional staffers' contact information by hackers, Congressman Lieu is now urging the Federal Communications Commission to take action quickly to fix the problem with SS7. The hackers are purportedly tied to Russian intelligence.
The vulnerability in SS7 was revealed in a presentation at the RSA security conference in March. It exploits the use of SS7 by cellular networks to handle billing and phone location data for call routing. The vulnerability is open to anyone with access to SS7 signaling. This includes not just telecommunications companies that have "roaming" relationships with a phone's primary carrier, but any state actor or hacker who has access to those companies' networks. Using SS7, an attacker could create a proxy to route calls and text messages. He could intercept them and record them without the knowledge of the people on either end of the communications. An attacker could also spoof texts and calls from a number.
"In light of the recent cyber hack at the [Democratic Congressional Campaign Committee] that released cell phone numbers of all Democratic Members of Congress—reportedly conducted by the Russian Government—our foreign adversaries can now acquire cell phone voice and text data of over 180 Congress members with impunity," Lieu wrote in a letter dated August 22. "This problem is particularly acute given reports that Russia is trying to influence elections in America."
Ordinary calls and texts aren't the only communications potentially at risk. The SS7 flaw may have been leveraged in a recent Iranian crackdown on users of WhatsApp, Telegram, and Instagram, in which 450 people were arrested or summoned. The people "were carrying out immoral activities, insulted religious beliefs, or had illegal activities in the field of fashion," a website tied to the Iranian Revolutionary Guard reported. Researchers recently demonstrated that they could break the security of WhatsApp and Telegram by using SS7 to redirect SMS traffic and obtain security codes to gain access to accounts.
Lieu urged FCC Chairman Tom Wheeler to "expedite investigation of the SS7 flaw" and report back on the progress of the investigation to Congress "so that we can respond appropriately to the recent hack... The SS7 problem is no longer a theoretical threat. Because we don't know how long hackers have had access to [congressional cell phone numbers], it is very possible that nearly half of Congress has already had voice and text data intercepted."
reader comments
64