Crooks are using hacked WordPress and Joomla sites to send massive amounts of spam using a complex botnet structure spread across seven different server layers.
The botnet had been known to security firms since 2014, but in its more recent incarnation, despite being smaller than its previous version, the botnet is harder to identify.
The first security firm to discover something fishy was Symantec in 2014, when the company's engineers kept founding the Spalooki malware on compromised Linux servers, which they presumed was used in some sort of spam operation.
More details came to light thanks to an Akamai SIRT report published in November 2015, which detailed the operations of an 83,000-strong botnet named Torte. Akamai said that crooks were compromising WordPress and Joomla sites through vulnerable themes and plugins, and using them for sending spam.
Torte botnet resurfaces as SpamTorte with improved infrastructure
In a report released this week, US-based cyber-security firm Verint says it uncovered a newer and improved version of the Torte botnet, which they named SpamTorte, currently comprised of only a few thousand bots.
In its 2015 report, Akamai described the Torte botnet as using a four-layer structure to carry out spam operations. Verint says the newer and improved SpamTorte variant uses a seven-layer system, with the C&C server sitting at the top, a layer of assembly servers beneath it, and five server layers for storing data for ongoign spam campaigns.
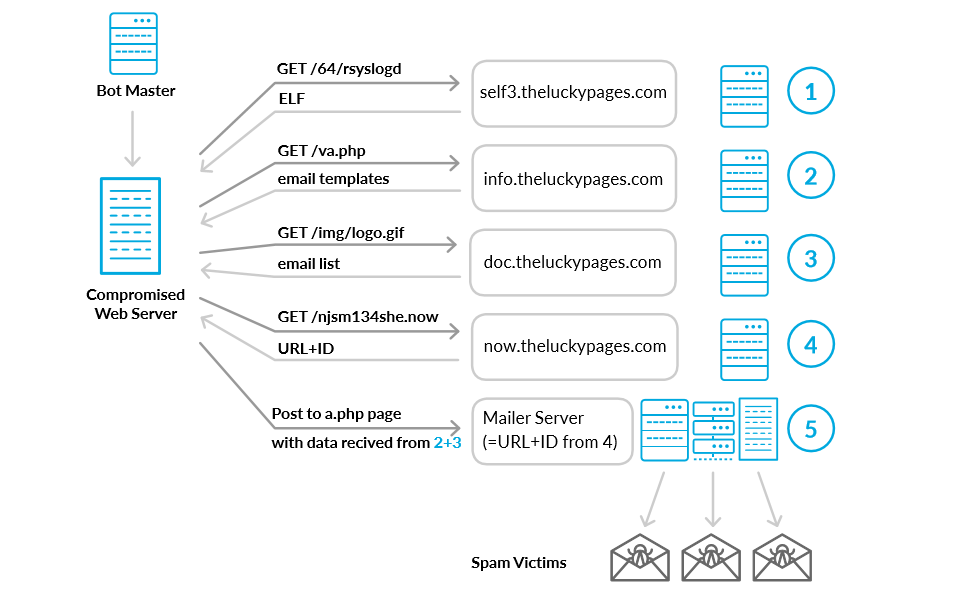
Verint has provided the image above to describe the infection process. All operations start with crooks finding vulnerable WordPress and Joomla CMS installations which they can hack leveraging various vulnerabilities.
The botnet operators are only interested in Linux servers and completely ignore Windows systems. Both 32-bit and 64-bit systems are supported.
Assembly servers used put together spam messages
Once they infect a server, the first step is to create a cronjob that downloads and re-downloads a malicious ELF binary from a "first level" servers. The repeated downloads act as a self-update system in case the malware author wants to update his bots.
After the ELF malware is downloaded and installed, it will contact "second level" servers, which will provide it with a collection of email templates.
The same operation is repeated by contacting "third level" servers, which will provide the malware with a list of email addresses.
The next step is to contact "fourth level" servers, which reply with a list of URLs that need to be inserted in the email templates, along with a campaign ID so the botnet's operators can keep track of different spam runs.
The last stage is to assemble the email templates and send them as base64 and XOR text to "fifth level" servers where the botnet operators have installed in advance mailer scripts that take care of sending out the actual spam.
SpamTorte botnet leveraged for adult and pharma spam
All these servers, spread across different levels, are hacked WordPress and Joomla sites. Verint says it detected the SpamTorte botnet sending out spam for various adult and pharma sites.
While the botnet is not as massive as the first version that Akamai saw in 2015, because this one is better compartmentalized, it's harder to identify and bring down.
"It is quite surprising that such a big spam operation is still active, but the layered structure of the botnet provides a nice cover," the Verint team writes in a report on SppamTorte's activities. "While the mailers are being blocked and blacklisted, the C&C servers remains undercover and untouched."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now